If you work IT in a Microsoft Active Directory environment, you may have experienced problems where a user’s account keeps getting locked out. Here’s a tutorial showing everything you need to know about how to track the computer that is locking any AD account.
Contents
Find Domain Controller Where Lockout Occurred
- Download Account Lockout and Management Tools from Microsoft on any domain computer where you have administrator rights.
- Create a folder named “ALTools” on your Desktop, then run “ALTools.exe” to extract the files to that folder.
- From the “ALTools” folder, open “LockoutStatus.exe“.
- Select “File” > “Select target“.
- Specify the “Target User Name” that keeps getting locked out and the “Target Domain Name“. If you’re not logged in as a domain administrator and would like to use alternate credentials, check the “Use Alternate Credentials” box, then type a domain account “User Name“, “Password“, and “Domain Name“.
- Select “OK“, and the user will be listed, along with the domain controller name where the account is getting locked.
Find Locking Computer Using Event Logs
- Login to the Domain Controller where authentication took place.
- Open “Event Viewer“.
- Expand “Windows Logs” then choose “Security“.
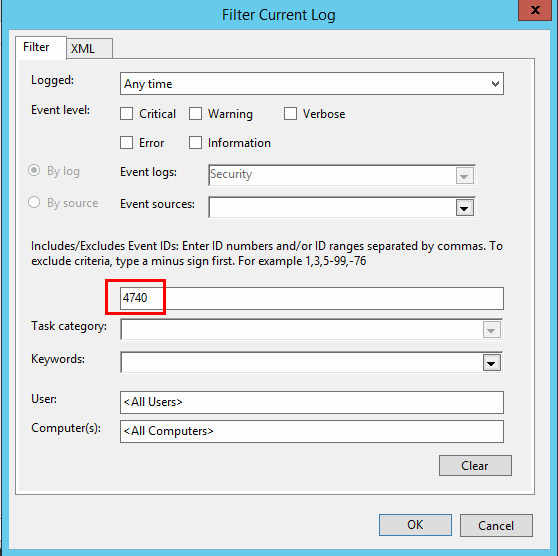
- Select “Filter Current Log…” on the right pane.
- Replace the field that says “<All Event IDs>” with “4740“, then select “OK“.

- Select “Find” on the right pane, type the username of the locked account, then select “OK“.
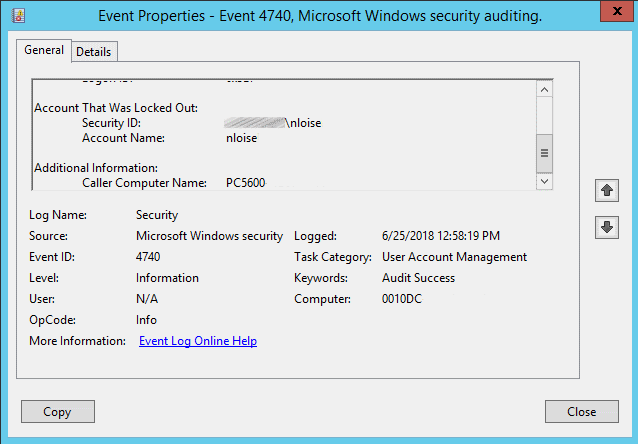
- The Event Viewer should now only display events where the user failed to login and locked the account. You can double-click the event to see details, including the “Caller Computer Name“, which is where the lockout is coming from.

Finding what Specifically is Locking Account on Computer
If the computer has been logged in since before the password for the account was changed or locked, a simple reboot may do the trick. Otherwise, follow these steps to check for stored credentials that might tied to a running a task and locking the account.
- Logon to the computer where the lockouts are occurring from.
- Download PsTools from Microsoft.
- Extract the single PsExec.exe file to “C:\Windows\System32“.
- Select “Start“, then type “CMD“.
- Right-click “Command Prompt“, then choose “Run as administrator“.
- Type the following, then press “Enter“:
psexec -i -s -d cmd.exe - Another command window will open up. Type the following in that window, then press “Enter“:
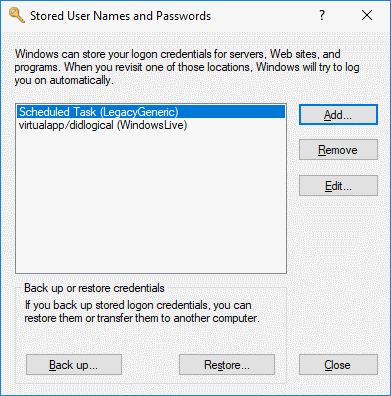
rundll32 keymgr.dll,KRShowKeyMgr - A window showing a list of stored usernames and passwords will appear. You can choose to “Remove” items from this list that may be locking accounts, or select “Edit…” to update the password.

FAQ
The Event Log tells me a computer name that doesn’t exist in our AD environment is locking the account. How do I track it down and stop it?
Most likely, somebody installed the Outlook app on a personal phone or tablet. The device is attempting to authenticate via a different device such as a Microsoft Exchange server. You can verify this with the following steps:
- Perform steps 1-6 as outlined above in the “Find Domain Controller Where Lockout Occurred” section.
- Login to the domain controller and enable debug logging for the Netlogon service.
- Wait for the lockout to occur again. Once it has, go back to the Lockout Status tool, right click the DC, then choose “Open Netlogon Log“.
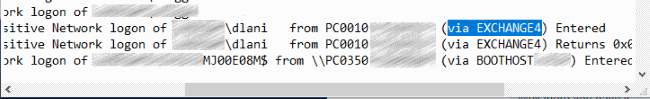
- Select “Edit” > “Find” and search for the locked username of the account. It should display the caller computer name followed by another computer name in braces where the requests are coming from.






Very helpful page in trying to find the source of a lockout. Very easy to understand.
Thank you! My client changed his password and didn’t realize that he was still logged into another computer.
You didn’t list one other place that can cause lockouts. Open local services, and sort by the “Log On As” column. Scroll through the list looking for the locked account. If a service is trying to use an old password, that’s guaranteed to lock an account.
Hi
I have been having problems for a very long time and I am trying to find out where the account lockout is originating from and I am unable to find out. So, I enabled netlogon on my domain controllers and I captured the first account lockout. This is what it shows, unfortunately there is no parenthesis and the source where it originated from. It says from DOMAINcontroller name Entered. So, could this domain controller itself be creating these account lockouts? If,, so how to fix it?
01/10 10:02:57 [LOGON] [9076] BCC: SamLogon: Network logon of domainname\adminaccount from Domain Controller Entered
Thank you. This is very helpful. I’m accessing the affected computer via PSexec as it’s offsite. Is there another way to look at the “stored username and password” that doesn’t require the window to be opened? Basically using CMD to do everything?
gerat article
Very useful article.