Anyone can become a victim of a data breach event. Here are the best data breach search engines to know whether your personal information is still secure.
In the present world, unauthorized use of personal and business data can cause irreversible loss to individuals and organizations.
Applying security measures at the personal level isn’t always enough for such incidents. A minor vulnerability on behalf of the websites that collect and store your data can be hazardous.
Contents
What Is Data Breach Search Engine?

Cyberattacks are on the rise, and sometimes, these attacks only intend to steal your personal and sensitive information to sell such data on the dark or deep web.
Using traditional search engines, it’s not always possible to know whether your data fell into the wrong hands or is up for sale. Because most of such stolen databases go into the dark or deep web.
You need one of the best search engines for the deep web. And for the dark web, well, that’s a bit complicated and risky. Read this article, “Access the Dark Web Safely: VPN for Dark Web,” to know more.
A more convenient and safe option is a data breach search engine. This search engine helps you instantly know if your data has been compromised. These search engines collect data that has been compromised recently or earlier.
You can easily find out about your compromised data and take necessary measures as the situation demands.
Why Do You Need to Use Data Breach Search Engine?
As mentioned before, data breach search engines are particular search engines. These are dedicated to finding out about the privacy of your personal information.
Using these search engines, you can effortlessly know if any of your email accounts or other information has been the victim of data breach incidents.
If you are unlucky and your data is not secure anymore, you can immediately change your credentials to stop further access to those accounts by criminals.
This will protect you from unauthorized purchases on eCommerce websites and identity theft.
You can even start using multi-factor authentication from now on and stop using those email addresses for your bank account.
1. Have I Been Pwned
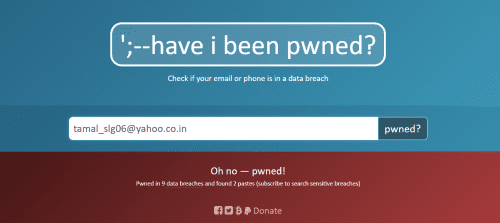
Have I Been Pwned is one of the most popular data breach search engines. Being one of the oldest in business, it’s also a free data breach search engine.
It has a collection of more than 12 billion compromised of breached accounts. To check, you need to enter your email address or phone number in an international format.
This search engine comes with a simplistic interface. If your entered data has been pwned, it shows you the data breach events during which hackers got access to your data.

Moreover, this search engine also shows brief information about those events and categories of data that got leaked, such as email id, password, name, username, geographic location, physical address, and social media accounts.
If you want to support this good cause, you can donate to this website that lets you perform a data breach database search.
2. DeHashed
DeHashed is another engine for search data. It has a collection of 14 billion compromised assets.
To check if any of your data has been compromised, you need to create an account on this website.
Then, select the field type such as emails, passwords, IP Addresses, usernames, names, phone numbers, VINs, and addresses before entering the data.
In case of breached data, it’ll show the number of events and their names. There is also the option to request entry removal for each incident.
It also shows you search results associated with data breach events, but you must be an active subscriber to enjoy this feature.
You can also use the DeHashed API for school projects and private use.
3. leakpeek

If you’re looking for a free data breach search engine, leakpeek is here. It has more than 8 billion records from which it can instantly find out about your query.
This data breach search engine can search five data types: email, username, password, keyword, and domain.
You can either type your query or paste it with one click. If you want to perform multiple searches, you can do those from the same page by clicking on Clear.
In case of data breaches, it shows you the passwords and the source name that consists of the website name from where the databases have been compromised.
4. mypwd
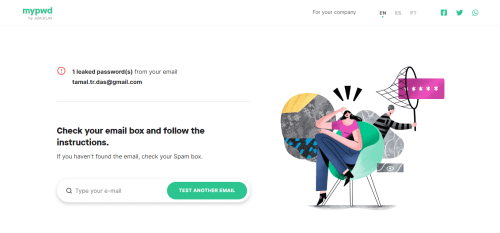
With mypwd, you can perform a data breach database search for free. It needs you to create an account with the email address you want to inquire about.
The website takes your privacy seriously. It sends your data breach-related information via an email to your registered address so that only the right person can access it.
The email contains the leaked password and the data breach event responsible for the compromised data.
Using this free database leak search engine, you can even track your organization’s email and password-leaking events.
5. BreachDirectory
BreachDirectory is another free data breach search engine that you can use to check whether you’ve been pwned.
For data breach database search, it searches through more than 9 billion records exposed in 120 data breach events.
You can check four categories using this: email, username, domain, and IP address. The results display the event names, brief information about those events, and the leaked data type.
You can even ask the website to notify you if the email address becomes compromised in the future.
Besides, this website collects various breach events, categories, record counts, and other additional information, like whether the data is sensitive, verified, or analyzed.
6. Leak-Lookup

Leak-Lookup is another data breach search engine. You must create an account on their website to check search data breaches.
Go to the dashboard, choose fields (username, IP address, domain, password, etc.), and enter your query to get detailed results. You can also select additional options.
It contains information on over 3800 events and 22 billion records. It also allows you to filter the reports and download them for sharing or personal reference.
7. Intelligence X

Intelligence X is a powerful yet free data breach search engine. With its help, you can enter your email, URL, IP, domain, Bitcoin address, and more.
You can also use its advanced search options for data breach database searches. The options include date filters, categories, public web of different countries, and domains.
You can even sort the search results as your choice and see result statistics in graph and chart format.
Data Breach Search Engine: Final Words
The data breach has become a common incident. Many people claim that every internet user has been the victim of a data breach at one time or another.
To know whether you are one of the victims, you can use data breach search engines. If you have any suggestions, add them in the comments.
Up next is how to text password strength.